Table of Contents
ToggleIntroduction
In today’s interconnected world, our digital footprint extends far and wide. From online banking to social media, from e-commerce purchases to subscription services, we rely heavily on passwords to protect our personal, financial, and professional information. As the gatekeepers of our digital lives, passwords play a pivotal role in safeguarding our data from prying eyes and malicious entities.
However, the increasing sophistication of cyberattacks and the methods employed by hackers have made it abundantly clear that not all passwords are created equal. A weak password can be the Achilles’ heel, providing easy access to cybercriminals, leading to identity theft, financial loss, and a host of other complications. On the other hand, a strong, well-constructed password acts as a formidable barrier, deterring unauthorized access and ensuring our online safety.
This article aims to shed light on the importance of strong passwords, the risks associated with weak password practices, and the steps one can take to fortify their digital defenses. As we delve deeper into the intricacies of password creation and management, we’ll equip you with the knowledge and tools needed to navigate the digital realm with confidence and security.
By understanding the significance and the mechanics of password security, we empower ourselves to take proactive measures, ensuring that our digital experiences remain both fruitful and secure.
Understanding the Basics of Password Security
The realm of password security is vast and intricate, but understanding its foundational principles is crucial for anyone navigating the digital world. Let’s delve deeper into what constitutes weak and strong passwords and the underlying reasons for their classifications.
What makes a password weak?
- Commonly Used Passwords: Surprisingly, many individuals still resort to using passwords like “123456,” “password,” or “admin.” These are among the first combinations hackers try.
- Dictionary Words: Passwords that are actual words or common phrases can be cracked using dictionary attacks, where hackers use software to quickly try thousands of dictionary words.
- Personal Information: Using easily accessible details such as your name, birthdate, or anniversaries is risky. Cybercriminals often research their targets and use this information to guess passwords.
- Keyboard Patterns: Sequences like “qwerty” or “asdfgh” might be easy to remember, but they’re also easy for hackers to guess.
What makes a password strong?
- Length: Every character added to a password increases its strength exponentially. Aim for at least 12-16 characters.
- Complexity: A mix of uppercase and lowercase letters, numbers, and special symbols makes a password harder to crack. It ensures that a hacker cannot easily use precomputed tables (like rainbow tables) to guess your password.
- Unpredictability: Avoid using obvious substitutions (e.g., “pa$$word”). Instead, think of random combinations or use phrases that only make sense to you.
- Absence of Repeats: Refrain from using the same sequence of characters repeatedly in a password, as patterns can be exploited.
Furthermore, it’s essential to understand that even the strongest password can be vulnerable if not handled correctly. For instance, sharing passwords, writing them down in easily accessible places, or using the same password across multiple platforms can compromise its strength.
In essence, a robust password is not just about its composition but also about the practices surrounding its use. As we continue, we’ll explore how to create and manage strong passwords effectively, ensuring optimal security in the digital space.
Steps to Create a Strong Password
Creating a strong password is both an art and a science. It’s about striking a balance between making it difficult for hackers to crack while ensuring it’s memorable for the user. Here’s a detailed exploration of the steps to craft a robust password:
Start with a memorable phrase or sentence
- Use Personal Experiences: Think of a unique personal memory, quote, or event. For instance, “My cat Fluffy jumped over the moon in 2019!” can be abbreviated and modified to “MCFjOtm’19!”
- Song Lyrics and Book Quotes: Use your favorite song lyric or book quote as a starting point and then modify it with numbers and symbols.
Use a mix of characters
- Uppercase and Lowercase Letters: This increases the number of possible combinations a hacker has to try. For instance, “applepie” can become “aPpLePiE.”
- Numbers: Integrate numbers in a way that’s meaningful to you but not obvious to others. Avoid using easily guessable numbers like “1234” or your birth year.
- Special Symbols: Incorporate symbols like !, @, #, $, etc., to add complexity. For instance, “I love chocolate” can become “I<3Choco!”
Avoid using easily accessible personal information
- Public Records: Details like your name, family members’ names, or address are often publicly available. Refrain from using them in your passwords.
- Social Media: Be wary of using information you’ve shared on social media platforms, as hackers can use this data to make educated guesses.
Consider using a password generator
- Randomness: Password generators create passwords by combining random characters, ensuring high unpredictability.
- Customization: Many password generators allow you to set criteria, such as length or types of characters used, ensuring the password meets specific requirements.
- Storage: If you’re using a password manager with a built-in generator, it will store the generated password securely, so you don’t have to remember it.
- In conclusion, creating a strong password requires a thoughtful approach. It’s about understanding the potential vulnerabilities and crafting a password that addresses them. With the right techniques and tools, you can ensure that your passwords are both robust and user-friendly.
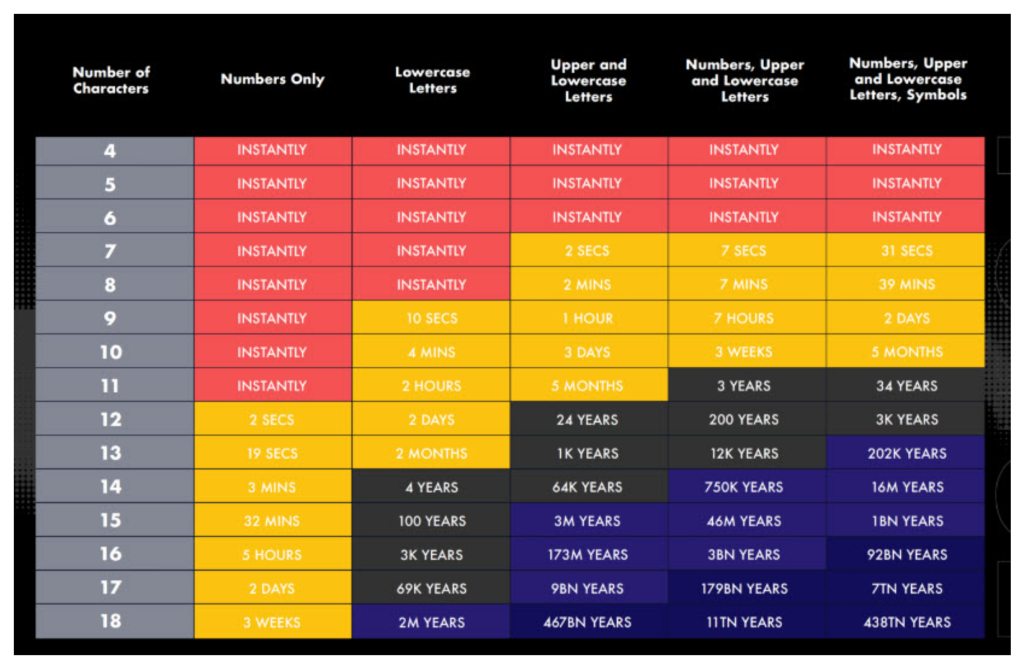
This chart provides an estimation of how long it would take to crack a password based on its complexity and length.

Best Practices for Keeping Your Password Safe
While creating a strong password is the first step, maintaining its integrity and ensuring its safety is an ongoing process. As cyber threats evolve, so should our practices to safeguard our digital assets. Here’s a detailed exploration of the best practices to keep your passwords secure:
Regularly update your passwords
- Scheduled Changes: Set reminders to change your passwords every 3-6 months. Regular updates reduce the window of opportunity for unauthorized access.
- Avoid Recycling: When updating, refrain from using slight variations of previous passwords. Each new password should be unique.
Avoid using the same password for multiple accounts
- Diversify Passwords: Each account should have its distinct password. If one account gets compromised, others remain safe.
- Prioritize Critical Accounts: Especially ensure that high-risk accounts like email, banking, and work-related platforms have unique and strong passwords, as they can be gateways to other sensitive data.
Be cautious of phishing attempts and unsolicited password reset emails
- Verify Before Clicking: Always double-check the sender’s email address and the content of the message for any suspicious elements. Authentic organizations will rarely ask for personal information via email.
- Use Direct Login: Instead of clicking on links in emails, manually type the website’s URL into your browser or use bookmarks to access sites.
Enable two-factor authentication (2FA) where possible
- Extra Layer of Security: 2FA requires a second form of identification beyond just a password, such as a text message code or biometric verification.
- Diverse 2FA Methods: Use different 2FA methods for different accounts when possible. For instance, use text message verification for one account and a mobile app like Google Authenticator for another.
Be wary of public Wi-Fi
- Unsecured Networks: Public Wi-Fi networks, like those in cafes or airports, are often unsecured and can be hotspots for cyberattacks. Avoid accessing sensitive accounts on these networks.
- Use a VPN: If you must use public Wi-Fi, ensure you connect through a Virtual Private Network (VPN) to encrypt your data transmission.
Regularly check account activity
- Monitor for Unusual Activity: Periodically review the activity logs of your accounts, especially financial ones, to detect any unauthorized actions.
- Set Up Alerts: Many platforms offer notification settings for unusual account activities. Enable them to stay informed.
In conclusion, while technology provides us with tools to create strong passwords and secure our data, human vigilance remains paramount. By adopting and consistently practicing these safety measures, you can significantly reduce the risk of your passwords falling into the wrong hands.
What to Do If Your Password is Compromised
Realizing that your password may have been compromised can be alarming. However, swift and informed action can mitigate potential damage and restore security. Here’s a detailed guide on the steps to take if you suspect or confirm that your password has been breached:
Immediate steps to take
- Change the Compromised Password: The first action should be to change the affected password. If you’ve used the same password on other accounts, change those as well.
- Check for Unauthorized Activities: Review the account’s activity logs to identify any unfamiliar actions, such as unauthorized purchases, messages, or profile changes.
- Contact the Platform: Inform the service provider or platform about the breach. They might have additional security protocols or can monitor the account for suspicious activities.
Monitoring for suspicious activity
- Set Up Alerts: If the platform offers it, enable notifications for unusual account activities. This will keep you informed in real-time.
- Review Linked Accounts: If the compromised account was linked to other services (e.g., a Google account linked to various apps), check those services for unauthorized activities as well.
- Monitor Financial Statements: If the breach involved financial accounts, regularly review your bank and credit card statements for unauthorized transactions.
Importance of informing relevant authorities or platforms
- Identity Theft Concerns: If you believe the breach could lead to identity theft, report it to local law enforcement and consider informing your country’s primary agency responsible for handling such issues.
- Financial Institutions: If banking or credit card information was involved, notify your bank or credit card company. They can monitor your accounts for fraudulent activities and may offer additional protective measures.
- Credit Monitoring: Consider subscribing to a credit monitoring service, especially if sensitive personal information was exposed. These services can alert you to changes in your credit report, indicating potential identity theft.
Preventive Measures for the Future
- Educate Yourself: Familiarize yourself with common phishing tactics and scams to avoid falling for them in the future.
- Regularly Update Software: Ensure that your operating system, browsers, and security software are up-to-date. Software updates often contain patches for known vulnerabilities.
- Backup Data: Regularly backup important data. If a breach involves ransomware, having a backup can prevent data loss.
In conclusion, while a compromised password can be distressing, taking informed and prompt action can help contain and rectify the situation. By being proactive and vigilant, you can enhance your digital security and navigate the online world with greater peace of mind.
Conclusion
The digital realm, with its vast opportunities and conveniences, also brings forth challenges in the form of security threats. As our reliance on online platforms grows, so does the importance of safeguarding our digital identities. Passwords, often the first line of defense, play a pivotal role in this security framework.
Throughout this guide, we’ve emphasized the significance of strong passwords, the potential risks of neglecting password security, and the measures one can adopt to ensure optimal protection. Crafting a robust password is not merely a technical exercise but a commitment to digital safety. By understanding the nuances of password creation, management, and response strategies in case of breaches, we equip ourselves with the tools to navigate the online world securely.
However, it’s essential to remember that the digital security landscape is ever-evolving. As cyber threats become more sophisticated, our strategies to counter them must adapt and advance. Regularly updating our knowledge, staying informed about emerging threats, and adopting a proactive approach to digital security are crucial.
In closing, while technology provides tools and mechanisms to protect our digital assets, the responsibility ultimately lies with us. By prioritizing security, practicing safe online behaviors, and continuously educating ourselves, we can ensure a safer digital journey for ourselves and our communities.

