Introduction to iPhone Security and the Growing Threat
In the digital age, the security of our mobile devices is paramount. iPhones, renowned for their advanced security features, are not immune to the clever tactics of modern thieves. Recent reports have highlighted a concerning trend: the exploitation of iPhone security settings, particularly the recovery key, by thieves to gain control over iPhones and permanently lock out the owners. This article delves into the intricacies of this issue and offers comprehensive strategies to safeguard your iPhone against such vulnerabilities.
Understanding the Recovery Key Exploit
The recovery key is a critical component of iPhone security. It is a complex, 28-digit code that plays a pivotal role in protecting your Apple ID and associated data from online hackers. However, in the wrong hands, this key can become a tool for locking legitimate owners out of their devices and accounts. Thieves who manage to physically steal an iPhone and know the device’s passcode can exploit this feature, leading to potential data and financial loss for the owner.
Proactive Measures for Enhanced iPhone Security
Fortifying Your Passcode
- Use of Biometric Security: Implement Face ID or Touch ID for unlocking your iPhone. This approach significantly reduces the risk of passcode exposure in public spaces.
- Complex Alphanumeric Passcodes: Opt for a longer, more complex alphanumeric passcode that is difficult for others to decipher.
- Immediate Passcode Change: If you suspect that your passcode has been compromised, change it without delay.
Additional Security Layers
- Screen Time Secondary Password: Although not officially endorsed by Apple, setting up a secondary password through the iPhone’s Screen Time settings adds an extra layer of security. This step requires a secondary password before any changes to the Apple ID can be made.
- Regular Data Backups: Consistently back up your iPhone data via iCloud or iTunes. This practice ensures that your data can be retrieved in case of theft.
- Utilizing Alternative Cloud Services: For added security, store important photos and sensitive files on other cloud platforms like Google Photos, Microsoft OneDrive, Amazon Photos, or Dropbox.
Long-Term Strategies and Recommendations
Advocating for Enhanced Customer Support
The role of customer support in security incidents is crucial. There is a growing need for companies like Apple to provide more robust support options and authentication methods for users facing such security breaches. This approach will enable users to reset settings and recover their accounts more efficiently.
Emphasizing User Responsibility
Apple’s stance emphasizes the user’s responsibility in maintaining access to trusted devices and the recovery key. Understanding and adhering to this responsibility is key to preventing permanent lockouts.
Conclusion: Staying Ahead of Security Threats
In conclusion, while iPhone theft and data security are serious concerns, by taking proactive steps and staying informed about potential vulnerabilities, users can significantly bolster the security of their devices. It is a continual process of adapting to emerging threats and leveraging available tools and practices to safeguard your digital life.
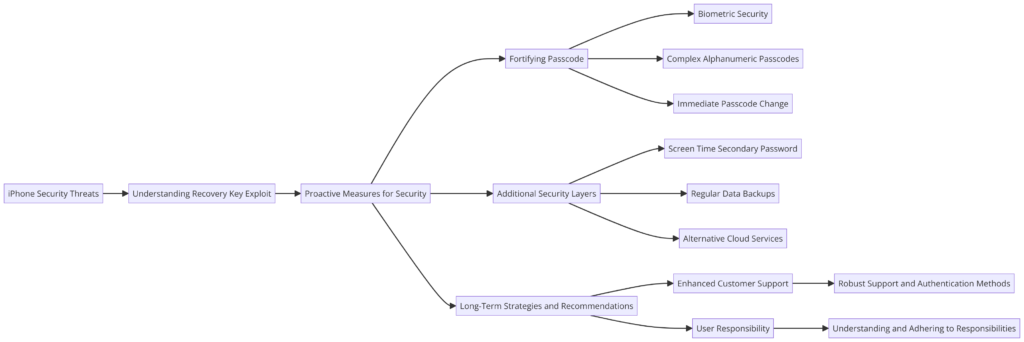
The diagram presented is a structured flowchart outlining a comprehensive strategy for enhancing iPhone security and mitigating risks associated with theft and unauthorized access. Here is an expanded explanation of each component and their interconnections:
iPhone Security Threats
- This is the starting point of the flowchart, highlighting the broad category of security threats that iPhone users may encounter. It sets the context for understanding the specific threat related to the recovery key exploit.
Understanding Recovery Key Exploit
- This section delves into the specific issue of the recovery key being exploited by thieves. It’s a critical juncture in the chart, as it transitions from general threats to a specific vulnerability that requires attention.
Proactive Measures for Security
- This node acts as a central hub, branching out into various strategies and actions that users can take to proactively safeguard their iPhones. It’s a key part of the flowchart, emphasizing user-initiated actions.
Fortifying Passcode
- This branch focuses on steps to strengthen the iPhone passcode, a primary defense mechanism against unauthorized access.
Biometric Security
- Includes using Face ID or Touch ID as secure and convenient methods of unlocking the iPhone, reducing the risk of passcode exposure.
Complex Alphanumeric Passcodes
- Advises on setting a more complex and longer alphanumeric passcode, which is harder to guess or observe.
Immediate Passcode Change
- Recommends changing the passcode immediately if there’s any suspicion that it has been compromised.
Additional Security Layers
- This section addresses the importance of adding extra layers of security beyond the basic passcode.
Screen Time Secondary Password
- Suggests setting up a secondary password through the Screen Time feature, adding an additional hurdle for anyone attempting to change the Apple ID.
Regular Data Backups
- Emphasizes the importance of regularly backing up data to iCloud or iTunes to ensure data recovery in case of theft.
Alternative Cloud Services
- Recommends using other cloud services for storing sensitive information, providing an additional backup and security layer.
Long-Term Strategies and Recommendations
- This branch of the flowchart addresses broader, more strategic approaches to enhance iPhone security over the long term.
Enhanced Customer Support
- Highlights the need for more robust customer support and authentication methods to aid users in recovering their accounts after security breaches.
User Responsibility
- Emphasizes the responsibility of users in maintaining access to their trusted devices and the recovery key, underscoring Apple’s policy on user accountability.
Robust Support and Authentication Methods
- This node is linked to the need for enhanced customer support, suggesting that companies like Apple should offer more comprehensive support options and authentication methods in security incidents.
Understanding and Adhering to Responsibilities
- The final node stresses the importance of users understanding and adhering to their responsibilities in terms of security, which is critical in preventing irreversible lockouts.
Overall, the diagram presents a holistic view of iPhone security, starting from recognizing the threats, understanding a specific exploit, and then branching into various preventive measures and long-term strategies to enhance security and user preparedness.